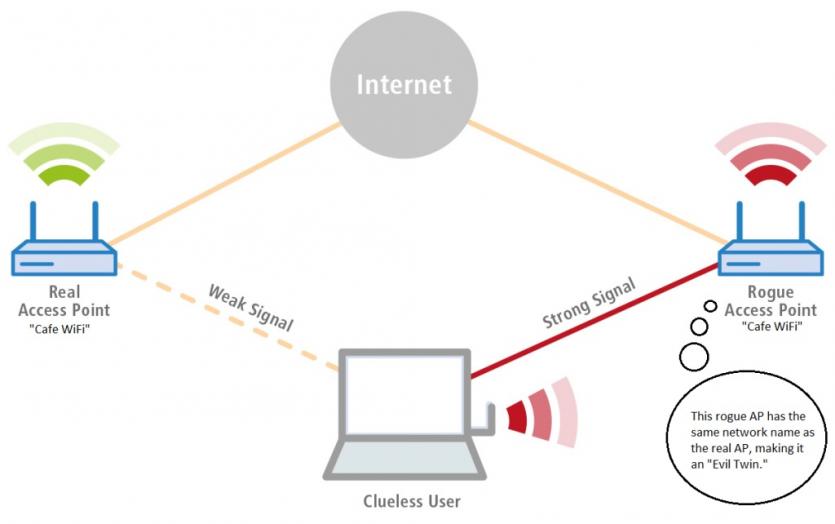
The Evil Twin attack is one of the common attacks around wireless networks, in which an attacker creates a fake wireless network, encourages users to connect to that network, and obtains their information to access their systems. In this attack, the fake network is identical to the name and identifier (SSID) of the real wireless network that users are trying to connect to. In other words, in the evil twin attack, the attacker creates a fake wireless network with a name similar to the real network and encourages users to connect to it in order to gain access to their personal and sensitive information.
By using this method, the attacker can get the sensitive information of the users, including the username and password, credit card number, mobile phone number and other personal and sensitive information. Also, the attacker can gain access to users' systems using this attack and use them as a gateway for other attacks. Organizations should use high security based wireless networks and also use methods to detect fake networks to prevent evil twin attack. For example, methods can be used to detect changes in the network identifier (SSID) and track the user's connection to wireless networks. Also, connecting to public and free wireless networks in public places is not recommended, as hackers often use these networks to trick users and steal their information.
Inadequate security in wireless networks
Statistics show that in most cases, wireless networks are implemented with the lowest security factor, which makes it easy for hackers to implement attacks like the evil twin. In general, important security weaknesses around wireless networks include the following:
Non-encryption of information: In wireless networks based on this model, information is exchanged between users and devices in a normal way. Because of this, attackers can easily obtain sensitive information. Unfortunately, some companies implement such networks with the aim of sending and receiving information faster.
Fake wireless networks: Attackers can create fake wireless networks and trick users into connecting to them. In this case, the attackers can get the sensitive information of the users and in some cases gain access to their systems.
Attacks using malicious software: attackers try to encourage users to install this type of software on their phones, tablets or laptops so that they can receive sensitive information in the easiest way and eavesdrop on users' information.
Failure to properly manage devices: In wireless networks, devices that are infected with vulnerabilities and have not received any patches pave the way for hackers to enter the network. That's why it's important that wireless devices, servers, and routers receive the latest security updates so that hackers have little chance of exploiting vulnerabilities.
To prevent these security problems from occurring, strong encryption protocols should be used, and antivirus and firewall software should be used. Also, the devices that connect to the network should be constantly monitored and updated and properly managed.
Pineapple WiFi Tool
WiFi Pineapple is a hardware device produced by Hak5 company and used to check the security of wireless networks. Typically, security experts use WiFi Pineapple to spoof wireless networks to identify security issues in their wireless networks. WiFi Pineapple has several features that allow users to easily check the security status of wireless networks, although hackers use this tool to implement the evil twin attack vector. This device can record wireless network traffic, collect user information to access systems, and simulate various types of attacks, including the creation of fake wireless networks. Due to the extensive capabilities that WiFi Pineapple has, this device is used as a penetration testing tool to check the security of wireless networks.
Bettercap tool
Bettercap is an open source security tool used to check and test the security of computer and wireless networks. This tool offers various possibilities for checking the security of wireless networks, including detecting devices connected to the network, injecting fake traffic into the network, conducting eavesdropping attacks, analyzing traffic, testing the encryption status of wireless networks, and detecting security threats.
Using Bettercap, you can easily scan wireless networks and identify their security issues. This tool uses various protocols to inject traffic into networks, including ARP spoofing and DNS spoofing, which allows users to monitor and analyze traffic.
Bettercap supports various encryption protocols such as WEP, WPA, WPA2 and WPS, allowing users to check the encryption of wireless networks. Also, this tool is capable of detecting security threats such as DoS attacks, MITM, ARP spoofing and other common attacks. It can be said that Bettercap is one of the useful and powerful tools for checking the security of wireless networks, but since this tool is also used for attacks, it should be used carefully and in compliance with security rules.
What is the evil twin attack?
As mentioned, the Evil Twin attack is one of the common attacks of wireless networks, in which an attacker creates a fake wireless network and encourages users to connect to that network and their information to access systems. They get it.
In this attack, the fake wireless network name and identifier (SSID) is very similar to the real wireless network, and the letters may have been changed or a character may have been added to the end of the network name. In such a situation, many users click on the button to connect to the network without paying attention to this issue and unintentionally connect to a network that is under the complete control of the hacker, and in this way their information is provided to the hacker. By using this method, the attacker can get sensitive user information and use it to implement other attacks or sell it on the dark web.
How does the evil twin attack work?
The evil twin attack is implemented with the aim of encouraging users to connect to a fake network, and its mechanism is as follows:
Creating a fake network: First, the attacker creates a fake wireless network with the same name and identifier (SSID) as the real wireless network that users are trying to connect to. In other words, the attacker creates a fake wireless network with a name similar to the real network name.
Encouraging users to connect: The attacker then encourages users to connect to their fake network. This is usually done by sending fake messages, attractive fake ads or sending fake emails to users.
Collecting information: After users connect to the fake network, the attacker can steal users' sensitive information such as usernames and passwords, credit card numbers, mobile phone numbers, and other sensitive information. Of course, in most cases, hackers use this attack vector with the aim of preparing a platform for implementing other attacks.
Hiding: The attacker tries to remain hidden to take full advantage of accessing users' sensitive information and using their systems for other attacks. For this purpose, the attacker uses various methods, including deceiving traditional firewalls, bypassing common security mechanisms, etc.
To prevent the evil twin attack, high-level security algorithms and mechanisms such as WPA2 or WPA3 should be used along with methods to detect fake networks. For example, methods can be used to detect changes in the network identifier (SSID) and track the user's connection to wireless networks.
What tools do hackers use to implement this attack vector?
As a security expert, you should know about the tools that hackers use to implement such an attack so that you can take the necessary precautions. Among the famous and widely used tools in this field that security experts use to identify weaknesses, while hackers use them to implement cyber attacks, the following should be mentioned:
Pineapple WiFi Tool
WiFi Pineapple is a hardware device produced by Hak5 company and used to check the security of wireless networks. Typically, security experts use WiFi Pineapple to spoof wireless networks to identify security issues in their wireless networks. WiFi Pineapple has several features that allow users to easily check the security status of wireless networks, although hackers use this tool to implement the evil twin attack vector. This device can record wireless network traffic, collect user information to access systems, and simulate various types of attacks, including the creation of fake wireless networks. Due to the extensive capabilities that WiFi Pineapple has, this device is used as a penetration testing tool to check the security of wireless networks.
Bettercap tool
Bettercap is an open source security tool used to check and test the security of computer and wireless networks. This tool offers various possibilities for checking the security of wireless networks, including detecting devices connected to the network, injecting fake traffic into the network, conducting eavesdropping attacks, analyzing traffic, testing the encryption status of wireless networks, and detecting security threats.
Using Bettercap, you can easily scan wireless networks and identify their security issues. This tool uses various protocols to inject traffic into networks, including ARP spoofing and DNS spoofing, which allows users to monitor and analyze traffic.
Bettercap supports various encryption protocols such as WEP, WPA, WPA2 and WPS, allowing users to check the encryption of wireless networks. Also, this tool is capable of detecting security threats such as DoS attacks, MITM, ARP spoofing and other common attacks. It can be said that Bettercap is one of the useful and powerful tools for checking the security of wireless networks, but since this tool is also used for attacks, it should be used carefully and in compliance with security rules.
How Hackers Implement an Evil Twin Attack
When security experts intend to identify the evil twin attack, they must first be familiar with how these networks are implemented. An evil twin attack is a type of network attack in which an attacker creates a fake wireless network to entice users to connect to it and exploit their information; For this purpose, the attacker seeks to create a fake wireless network with the same name as the real network and informs the target users that the new network is the best option to connect to the Internet. Due to the similarity of the network name, the users connect to the fake network, as a result, all the traffic of the user's network passes through the fake network and the attacker can benefit from the users' information. The steps to implement the evil twin attack are as follows:
Finding the real network name: The attacker needs to find the real network name and look for its similarities to create a fake network with the same name.
Creating a fake network: The attacker must create a fake network with a name similar to the real network. This network is built away from the eyes of the network owner and usually devices like WiFi Pineapple or software like Airgeddon are used to build it.
Notifying users: The attacker sends messages to users to connect to the fake network. For this, the attacker uses various methods, including sending advertising messages, displaying fake web pages, or even sending short messages.
Collecting information: after connecting users to the fake network, the attacker can see all their traffic and abuse their information. This information can include username, password and other sensitive information that users have entered while using the fake network.
Maintaining access: To maintain access to users' traffic, the attacker must keep the fake network stable and use various methods to prevent users from connecting to the real network. For example, an attacker can use techniques such as deauthentication and disassociation to keep users away from the real network and redirect them to the fake network.
It should be noted that the evil twin attack around wireless networks is quite serious and dangerous and can cause unauthorized access to users' sensitive information. For this reason, it is very important to use secure wireless networks and implement security techniques such as implementing encryption and activating security protocols such as WPA2 and WPA3.
Can a fake wireless network be detected easily?
It is very difficult to recognize a fake wireless network because its name is not much different from the original network name. An attacker can create a network with the same name as the original network using tools such as fake wireless network creation software. This fake network can act like the original network and allow users to access the Internet, but at the same time, the attacker can monitor and obtain all the information sent and received. However, there are some methods to detect a fake wireless network. For example, some security tools such as network traffic monitoring programs are capable of detecting fake networks. In some cases, these tools can distinguish the fake network from the real network based on the difference in the network name and ID. In general, detecting a fake wireless network is very difficult and requires technical knowledge and the right tools. Therefore, the best way to prevent evil twin attacks is to use secure wireless networks with strong encryption.
Strategies to deal with the evil twin attack
Security experts have different strategies to deal with the evil twin attack, the most important of which are the following:
Use secure wireless networks: Using wireless networks with security protocols such as WPA2 significantly reduces the incidence of wireless evil twin attacks. These protocols use strong encryption to protect your information from phishing attacks.
Updating devices: Updating mobile devices and wireless devices to the latest software versions reduces the chance of this type of attack occurring, as updates usually increase device security.
Do not connect to unknown wireless networks: Connecting to unknown and unencrypted wireless networks, including networks called Free Wi-Fi or Public Wi-Fi, is not a wise thing to do. It is better to make sure that the wireless network you are connecting to is valid and secure.
Using a virtual private network: Using a virtual private network to connect to the Internet reduces the incidence of evil twin attacks. By using a virtual private network, your traffic is encrypted, making it impossible for attackers to access your information.
Using security tools: Using security tools like WiFi Inspector or Fing will help you to check the wireless networks in your environment and identify fake networks.
Educating users: Informing and educating users prevents hackers from successfully implementing fake wireless networks and exploiting them. It is better to train users to connect only to networks that are trusted and to use strong encryption to protect their information.
Make it a habit to check the network name: Always make sure that the network name matches the original network name before connecting to a wireless network. If there is any change in the name, first contact the IT department of the organization and then connect to it.
Using network monitoring software: Using network monitoring software such as Wireshark allows you to identify this network model in the shortest time. By using these softwares, you can monitor your network traffic and react quickly if any fraudulent activity is detected.
Finally, to reduce the possibility of an evil twin attack, you should always pay attention to the security of your wireless network and use appropriate security methods.
last words
There are some other important points about the attack of the evil twin that it is not inappropriate to mention them at the end of the article.
Evil twin attacks can be done using relatively simple software tools; To implement an evil twin attack, an attacker does not need special tools and software because these tools are readily available on the Internet and do not require great technical knowledge to use them.
This attack is common in public environments such as airports, cafes, hotels, etc. Evil twin attacks are very common in public environments where public wireless networks exist. Especially in places where many people use wireless networks to perform various and sometimes sensitive tasks. An attacker can access your information through this attack vector. If the attacker has the ability to create a fake network, he can access your information, so do not transmit your personal information while using public networks.
Evil twin attacks may be carried out anonymously. In many cases, attackers are able to carry out evil twin attacks anonymously. This means that they can easily create a fake network and access user information without being detected.
Some security tools may fail to detect evil twin attacks. For example, if an attacker uses a wireless network with the same name as the original network, some network monitoring tools may not detect this attack.
Generally, public wireless networks and evil twin attacks are two intertwined concepts, as many public wireless networks are implemented without encryption or using weak encryption, which increases the chances of hackers to implement evil twin attacks.
Using a virtual private network can protect you against this type of attack in some cases. Using a virtual private network, your internet traffic is encrypted and all the information you exchange on the network is sent and received encrypted.
Finally, it is important to be aware of the different methods that hackers use to implement this network model. For this reason, it is recommended to increase your knowledge about these attack vectors.